Email & marketing automation
Create, automate, and optimize email campaigns using customer data and flexible workflows

Reach your audience instantly, everywhere: connect Google accounts to Copernica
Why choose Copernica for email & marketing automation?
Everything you need to design, automate, track, and personalize email campaigns in one platform

Email editor
Design and customize responsive email templates with an intuitive editor

Database
Centralize and enrich customer data for highly targeted campaigns
Website tracker
Monitor website activity and trigger automated campaigns in real time

Automation
Automate personalized email workflows based on customer behavior

GDPR
Built-in GDPR tools to manage consent and customer data securely
Email & marketing automation in one platform
From email campaigns to advanced automation, powered by customer data
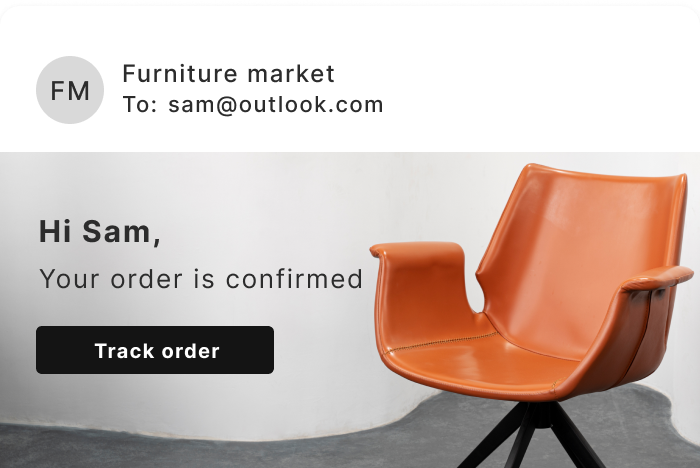
Built on decades of email expertise, Copernica empowers organizations with flexible, reliable, and personalized email communication.
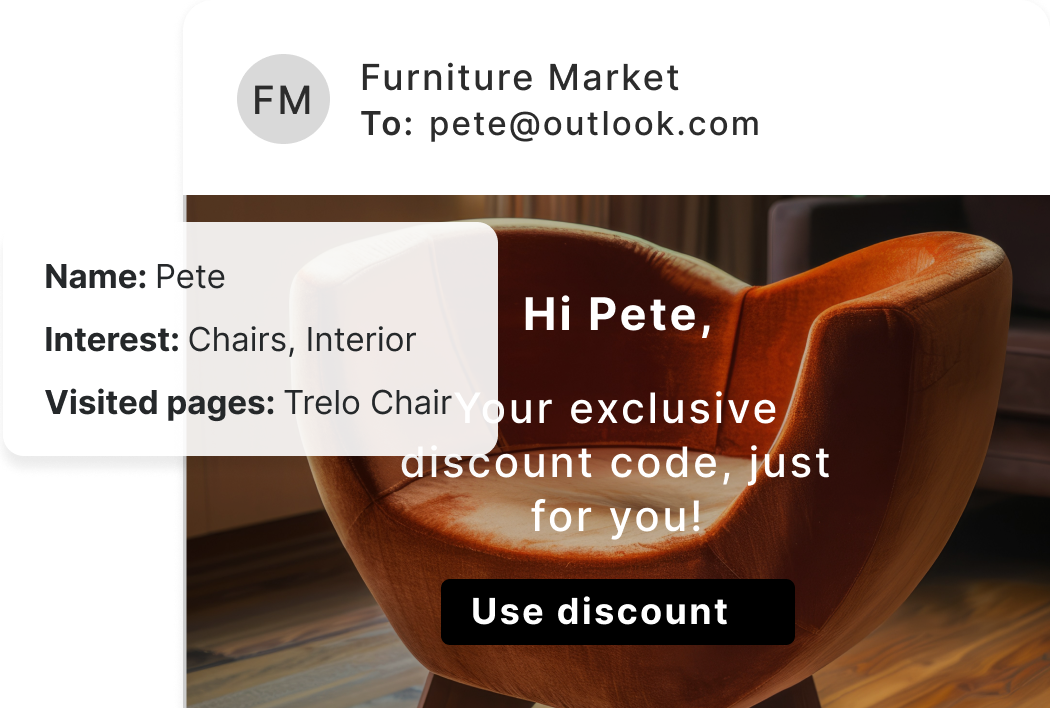
Marketing Automation
Copernica transforms customer data into smart, automated campaigns that reliably deliver the right message to the right customer at the right time.
Which Copernica product is right for you?
Copernica offers three different powerful solutions, tailor made for a specific audience and application
Discover below which product best suits your situation.
Experience it yourself
Our team can walk you through options tailored to your organization.
Start today
Curious about email or marketing automation?
Use customer data and flexible workflows to create, automate, and optimize campaigns. Let’s explore the possibilities together.

Bjorn Schneider
Sales
Customer success stories
An exclusive insight into the best email marketing campaigns, written in collaboration with our partners

Mailmeisters generates more revenue with these automations
With the right marketing automations, you can convert visitors into buyers, save time, and make every message feel personal. In this case, we show how Mailmeisters uses essential automations via Copernica to achieve immediate results and strengthen customer relationships
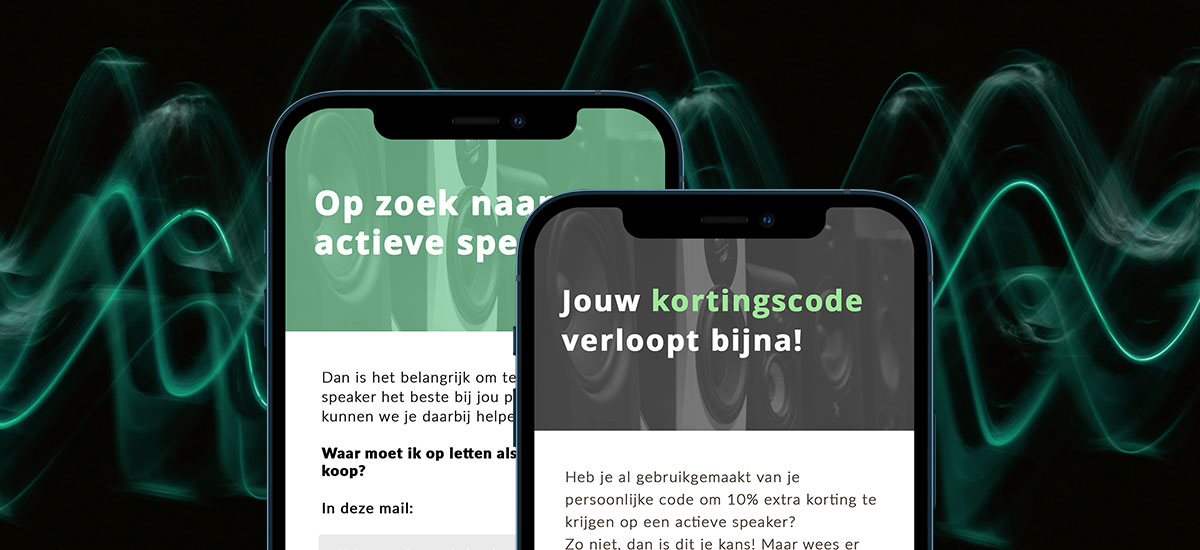
MaxiAxi achieves 705% growth in email marketing
With smart email automations, MaxiAxi boosted revenue by 705% in four years, improved efficiency, and made every customer touchpoint more meaningful. In this whitepaper, we show how phased campaigns and automated journeys helped them achieve rapid growth and measurable results.

Smartphonehoesjes boosted email revenue by 200%
Smartphonehoesjes.nl set up email campaigns based on website behavior, like an abandoned browser campaign that encourages visitors to complete their purchase. They also improved reactivation campaigns to re-engage inactive customers via email.
Backed by our partner network
Our 300+ partners extend the power of our software, helping you implement, customize, and maximize results
Copernica news
The latest news of Copernica, product updates, events and new features














